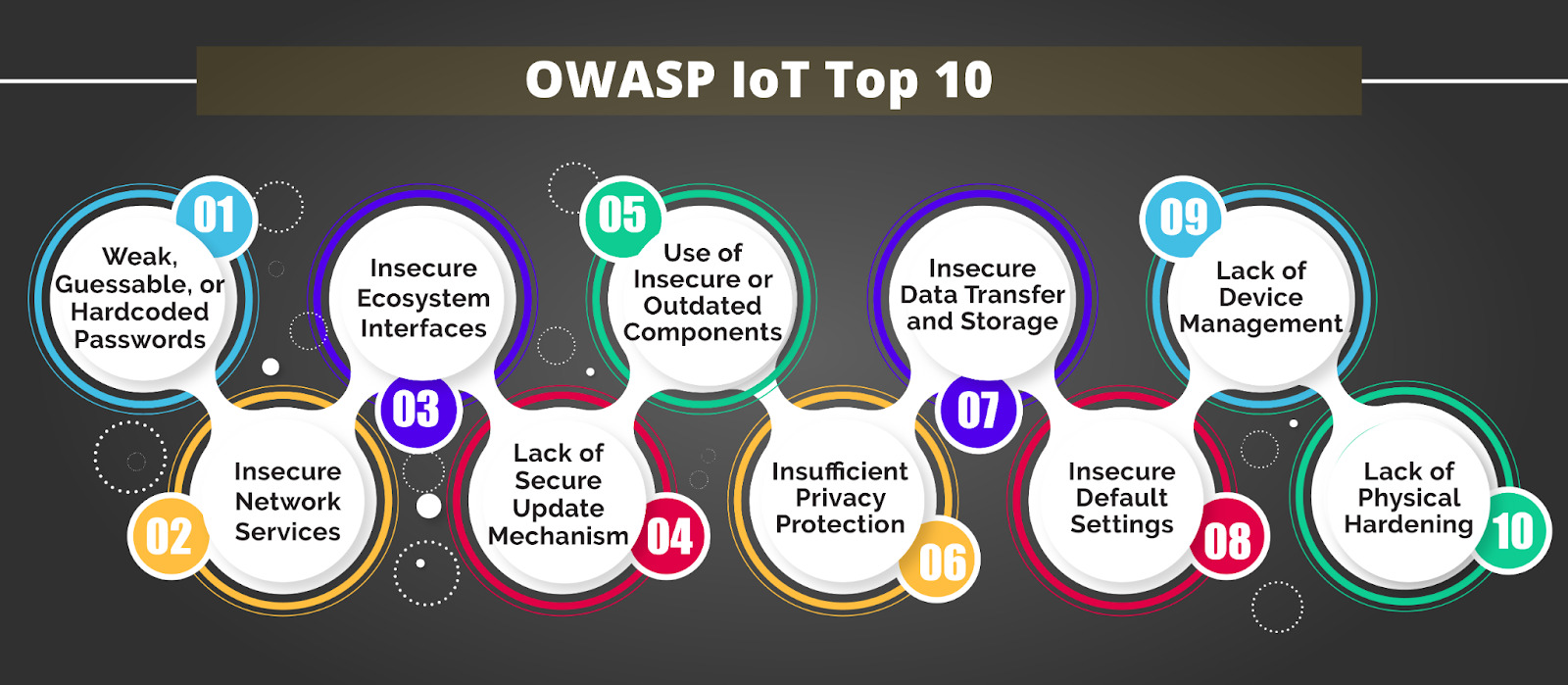
Introduction of the element of OWASP IoT Top 10 at the time of launching the applications is considered to be a very important aspect so that the development of the applications will be carried out in a very safe and secure manner. This particular aspect will be based upon a very cooperative testing plan along with robust security features so that things will be evident without any kind of doubt. This is the best approach to dealing with the local data storage and sensitive information very proficiently so that network connections will be perfectly introduced and further, there is no scope of any kind of hassle. OWASP IoT Top 10 is done as the best possible approach of manual and listing of the guidelines in such a manner that mobile application security development, testing and reverse engineering will be carried out very easily so that every concerned individual will be able to understand the techniques of mobile application security testing like a pro.
Some of the very basic technicalities which people need to understand associated with the concept of OWASP IoT Top 10 have been very well explained as follows:
- Mobile application security testing: This is based upon a comprehensive understanding of every phase of development right from the very beginning to being released so that everything will be sorted out very easily. In this particular manner things can be bifurcated into different kinds of options which are explained as follows:
- Vulnerability analysis: This is known as the best possible type of static analysis involved in the detailing system so that the source code will be understood very easily. This aspect will help deal with the loopholes and weak features without any doubt.
- White box testing: This is the exact opposite of the black box system and ultimately will be conducting more of this system with proper knowledge of the things without any doubt.
- Blackbox testing: Testing in this particular case will be behaving like a real attacker and ultimately will be exploring the best possible combinations for the publicly available and discoverable information.
- GRAY box testing: This is the sandwich option of black and white which will help provide people with a clear-cut idea about the credentials which are usually hidden.
- Penetration testing: This is known as the final or the near-final stages which will help make sure that planning right from the preparation to the information gathering and other associated things will be done without any kind of doubt.
- Mobile application architecture: Authentication for the mobile applications will be done in a very well-planned manner so that everyone will be able to deal with user credentials, sensitive information and other associated things very easily. It is very much important for people to be clear about the prominent methods in this particular case which are explained as:
- Stateful authentication: This is a very unique session ID that will be generated for every session and ultimately people will be able to deal with things very professionally without any kind of doubt.
- Stateless authentication: Entire information about the user in this particular case will be stored in a client-side token so that everything will be sorted out very easily and efficiently. In this particular manner, people will be able to deal with the maintenance aspect very easily so that everyone will be able to understand the multiple technicalities without any kind of problem. This is the best approach to improving scalability and performance.
- Testing network communication: This is the best possible approach to dealing with the network-connected mobile application systems so that everyone will be able to understand the layered security very proficiently. This is the perfect approach and attending the transmission of data between different kinds of remote endpoints so that everyone will be able to deal with the network security systems without any kind of problem. In this particular manner, people will be able to implement the strategy system very efficiently so that configuration of the system proxy will be done on mobile devices.
- Cryptography in the mobile applications: Cryptography in this particular case will help secure the data of the mobile applications very easily so that focus on confidentiality, data integrity and authenticity will be there very easily. Confidentiality in this particular case will help provide good control over the encryption and decryption so that the security of data will be there. Data integrity in this particular matter will help ensure that consistency will be there and further, there will be no scope for any kind of problem. Authenticity on the other hand will help invalidate the sources and users without any kind of hassle.
- Testing the quality of the coding: Different kinds of programming languages in this particular case will be significantly used so that framework will be understood very easily and further, there is no scope for any kind of problem. Testing the quality of the coding in this particular matter will help provide people with a good command of the technicalities so that SQL injection, buffer overflow and other associated things will be easily made available without any doubt.
Apart from the above-mentioned points remaining prepared for the future is considered to be a great idea for the organisation so focusing on the emerging technologies in this particular manner is a great approach. Introduction of the element of OWASP IoT Top 10 with the help of companies like Appsealing is the best possible approach to dealing with things in a very systematic manner so that everyone will be able to enjoy the best possible complete planning and execution without any hassle. This will help make sure the reporting, resolution and retesting will be taken into account very professionally and ultimately everyone will be able to enjoy every personalised experience. Remaining up-to-date in terms of technology is the perfect opportunity of keeping up the speed limit on top-notch systems so that emerging issues will be eliminated from the whole process without any kind of doubt. Runtime application self-protection will be helpful in real-time analysis of the applications so that everyone will be able to enjoy the upper hand over the attackers.